Industry challenges'
Why Secure Workplace?
From fostering a security conscious culture, to protecting user identities and devices remotely, our Secure Workplace services will keep your organisation and employees safe and secure.

Security starts at home
Employees, with all their good intentions, are often the weakest link in an organisation’s cybersecurity defences. Human error, whether through falling for phishing scams, clicking on malicious links, or mishandling sensitive data, can lead to devastating security breaches.
While social engineering is never going to go away, we can all mitigate their impact by implementing effective technology solutions and providing comprehensive training for employees.

Secure your identities
Critical data falling into the wrong hands can have a damaging impact. That’s why we have developed our Identity and Access Management (IAM) framework. IAM ensures that the right individuals have appropriate access to resources without compromising security.
We can also work with your teams to implement multi-factor authentication (MFA) as a standard routine. MFA adds an extra layer of protection and is especially useful to help you protect your most sensitive information.

Secure your devices
Many of us will work remotely for at least part of the week, and that means using our devices in the office, at home, and on the move.
To maintain security, our teams can work with you to introduce robust antivirus software for protection against malware threats. We can help you to implement Intrusion Detection systems (IDS) to detect and prevent unauthorised access. And we can also roll out Mobile Device Management (MDM) solutions to enforce policies and configurations for mobile devices.
Benefits of Secure Workplace from Logicalis
Unparalleled expertise and global reach
At Logicalis, our 7,000 Architects of Change operate across 30 territories worldwide. With a proven track record, we empower over 10,000 clients across diverse industry sectors to achieve sustainable outcomes through cutting-edge technology solutions.
Partner with us to elevate your organisation’s security posture and drive meaningful results.
End-to-End security guidance and execution
With over 25 year’s experience, Logicalis stands out by offering both advisory expertise and execution capabilities. Unlike many other companies that solely provide advice and then outsource implementation, Logicalis can guide your security strategy then make it all happen.
Trust us to be your comprehensive security partner, from planning to successful implementation.
Unrivalled compliance expertise
At Logicalis, our team of security experts possesses an intimate understanding of global compliance frameworks. This ensures that your company is meticulously aligned with the latest compliance laws and agreements.
Trust us to safeguard your organisation’s integrity and regulatory adherence.
Unrivalled SOC expertise
With over 15 year’s experience, Logicalis has cultivated a team of brilliant minds within our Security Operations Centre (SOC). Despite resource constraints in the industry, we’ve consistently attracted and retained top talent.
Trust us to safeguard your organisation with unparalleled expertise and dedication.
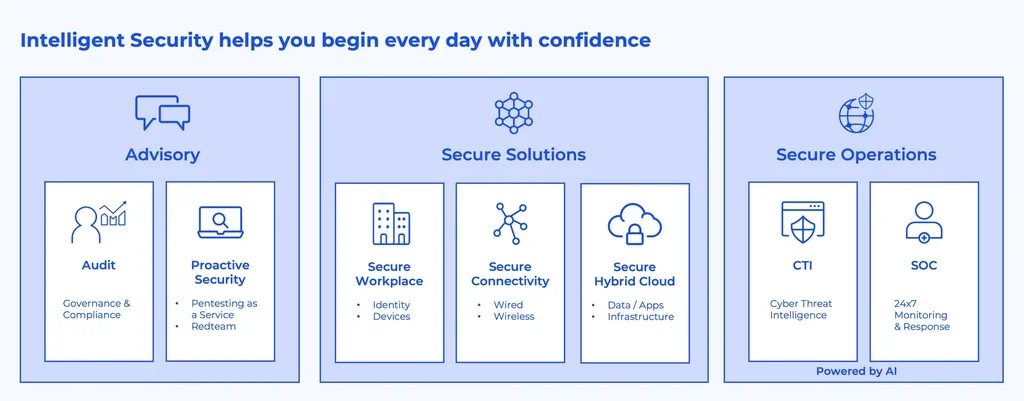
Ensure coverage through our Intelligent Security blueprint
The Logicalis Intelligent Security Blueprint offers comprehensive guidance for navigating today's complex security landscape.
By integrating security across an organization's infrastructure, from network to data and identity, Logicalis ensures a cohesive and robust defense strategy. The blueprint covers essential pillars, including Advisory for GRC consultancy, Secure Workplace for safeguarding communications and devices, Secure Connectivity for protecting the network, Secure Hybrid Cloud for managing data across environments, and Secure Operations for SOC services.
With Logicalis as a strategic security partner, organisations gain the tools and expertise needed to protect their business, assets, and customers effectively.
Our Secure Workplace Services

Managed SecOps
Managed Security Operations (SecOps) includes continuous monitoring, threat detection, incident response, and vulnerability management to enhance your organisation’s overall security posture.

Email security
Logicalis can provide email security to protect email accounts and communications from unauthorised access, loss, or compromise. We help organisations enhance their email security posture by establishing policies and using tools to safeguard against malicious threats such as malware, spam, and phishing attacks.

Endpoint Security
Endpoint security protects your individual devices (computers, laptops, and mobile devices) within the network. We implement a combination of antivirus software, firewalls, intrusion detection systems, and regular security updates to prevent unauthorised access, malware infections, and data breaches.

Mobile Device Management
Mobile Device Management (MDM) allows organisations to securely manage and control mobile devices (such as smartphones and tablets) used by its employees. Logicalis can help enforce policies, configuring settings, distributing applications, and monitoring device health to ensure data protection and compliance.

Modern App Delivery
Logicalis’ Modern Application Delivery service allows you to deploy software in a fast, consistent, and reliable manner while maintaining high security standards.

Multi-factor Authentication
Multi-factor Authentication (MFA) enhances your security posture by ensuring users present two or more pieces of evidence (password, USB key, fingerprint etc) prior to accessing mission critical files.

Identity / Access Management
Identity and Access Management (IAM) is a framework that ensures only authorised individuals have appropriate access to an organisation’s resources, systems, and data. It involves managing user identities, authentication, authorisation, and permissions to maintain security and compliance.

Access controls and policies
Access controls determine who can access specific resources (such as files, databases, or systems) and what actions they can perform. Policies, on the other hand, define rules and guidelines for managing access, authentication, authorisation, and data protection. Together, they help maintain a secure environment by ensuring that only authorised users have appropriate access to sensitive information.
Customer success story

Fortifying global gaming security: A Logicalis Intelligent Security success story
Logicalis has successfully transformed the security infrastructure of a global lifestyle brand for gamers by deploying advanced MXDR capabilities. This initiative significantly enhanced security efficiency, reduced operational costs, and improved the customer's security posture and resilience.
The partnership underscores the value of innovative technologies and expert guidance in navigating cybersecurity threats, reaffirming Logicalis' position as a trusted security partner.
Our partners
We work with leading global partners to deliver our Secure Workplace services and solutions.


Latest resources
Press release: Microsoft verified managed XDR status
Logicalis joins an elite group of managed service providers certified to deliver Microsoft’s most advanced managed detection and response services worldwide

Press Release: Tenth annual Logicalis CIO Report 2024 finds 63 per cent of Australian CIOs prioritise artificial intelligence
Discover more of the top priorities of tech leaders according to the Logicalis 2024 CIO Report. Learn about AI, digital transformation, and cybersecurity investments amidst economic uncertainty.

Blog: Intelligent Connectivity powered by Cisco
The Logicalis and Cisco partnership goes from strength to strength as Logicalis achieves the Cisco Powered validated service for Secure Access Service Edge (SASE) and SD-WAN status.

Be the guardian of your digital future
Innovate and advance. Be where you want to be, following an Intelligent Security blueprint for success with Logicalis by your side.
Get in contact with us today


